The Users page is where you manage individual people who can sign in to Cedar.
How to invite a user
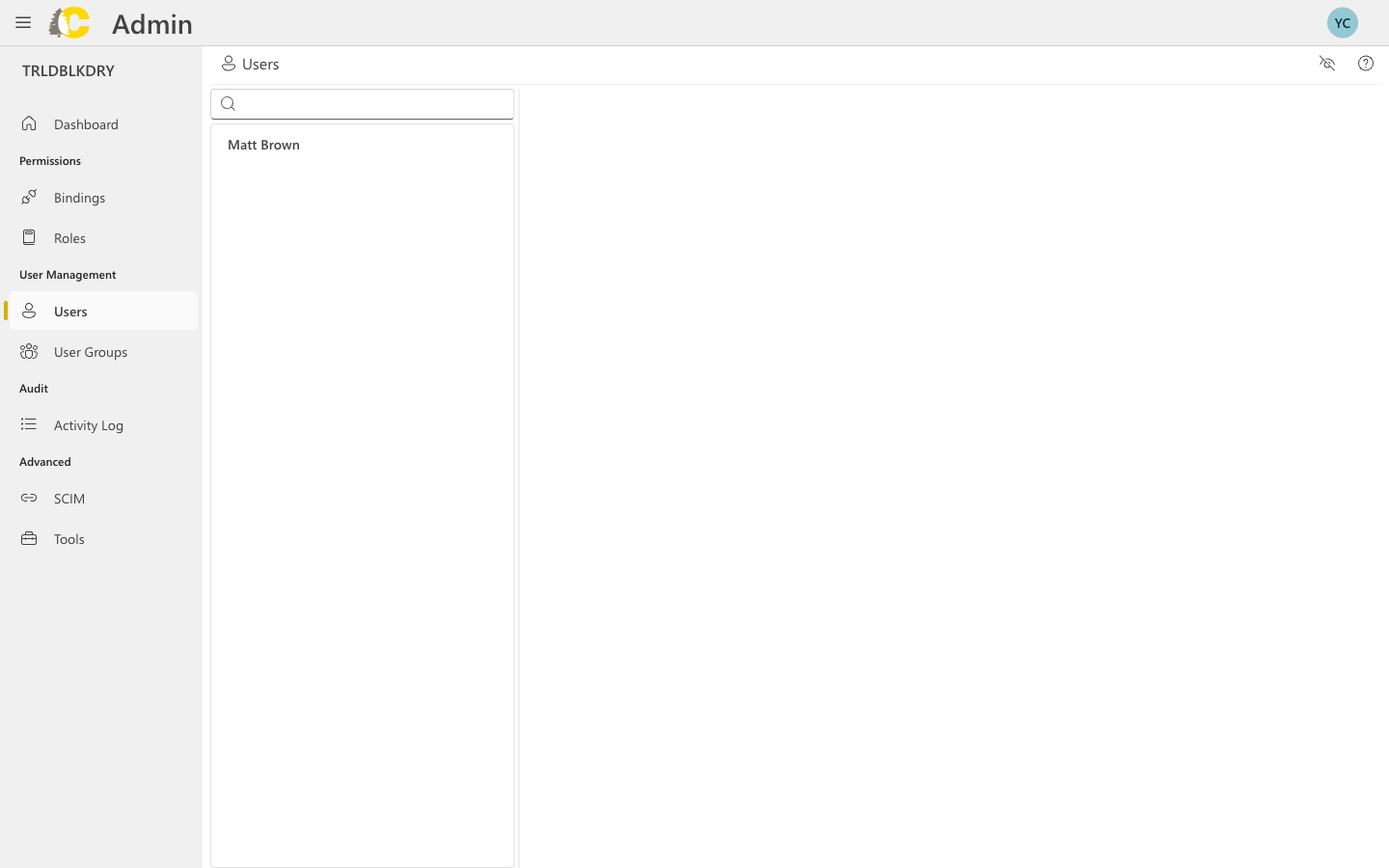
Users are invited through the User Groups page. When you invite a user, they’re automatically added to the group — this ensures every user has proper access from the start.Click the add user button
In the Users in Group section, click the + button to open the invitation dialog.
Enter the user's email
Type the user’s email address and click Add to add it to the list. You can add multiple emails.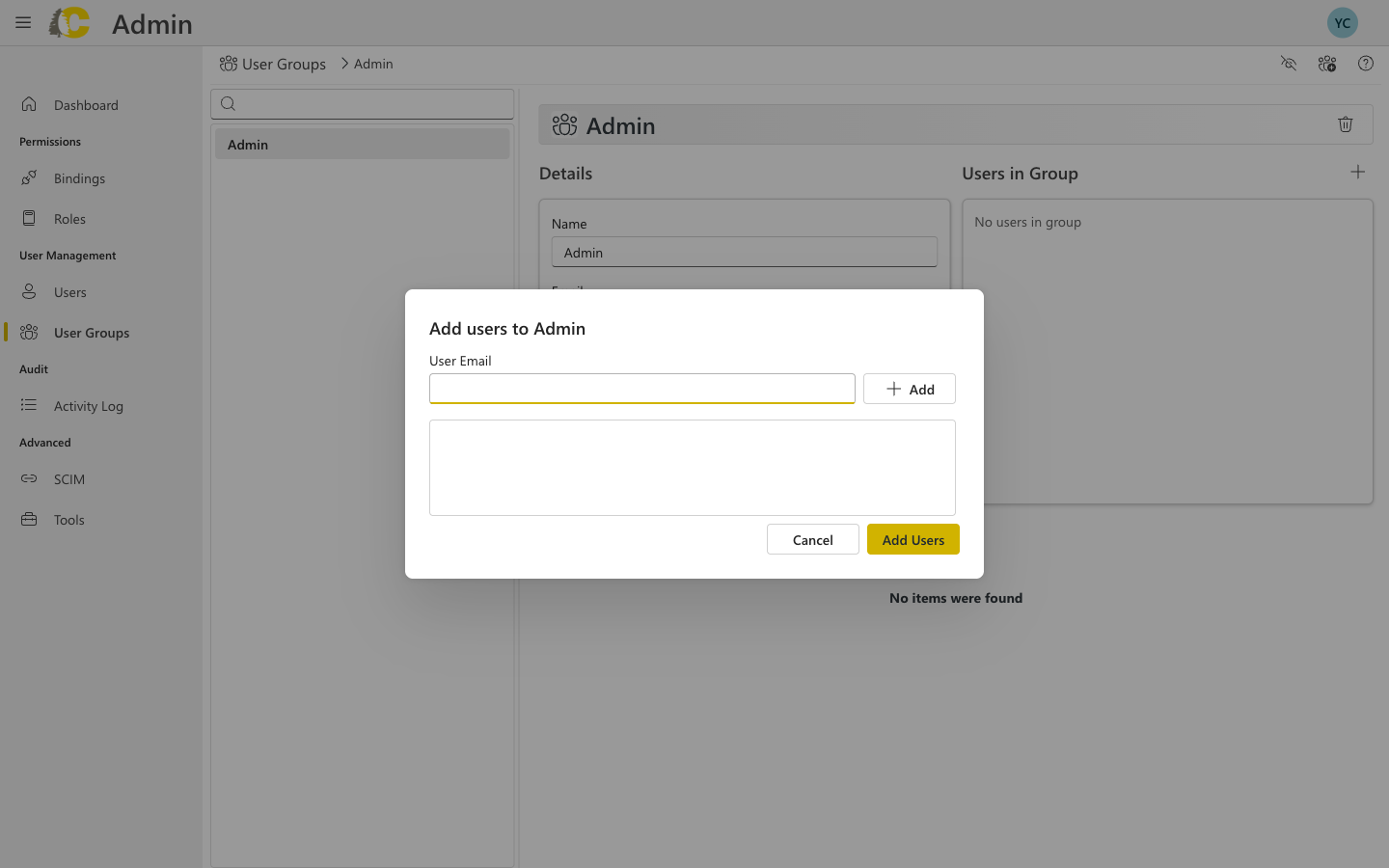

Why invite through groups? This design ensures users always have proper access. A user without group membership has no permissions, so inviting directly into a group streamlines onboarding.
How to add an existing user to another group
If a user already exists and you want to add them to an additional group:If the user already exists, they’ll be added to the group immediately without receiving a new invitation email.
Users inherit all role assignments from their groups. This is the preferred approach over assigning roles directly to individuals.
How to check why a user can’t log in
When someone reports they can’t access Cedar, follow these steps to investigate.Check their status
Look at the Status column:
| Status | Meaning |
|---|---|
| Registered | Account is active and ready to use |
| Pending | Invitation sent but not yet accepted |
| Disabled | Account has been deactivated |
Verify the email
Make sure the email address matches exactly what the user is trying to sign in with.
Check group memberships
Open the user detail panel and verify they belong to a group that has the necessary role bindings for what they’re trying to access.
User details view
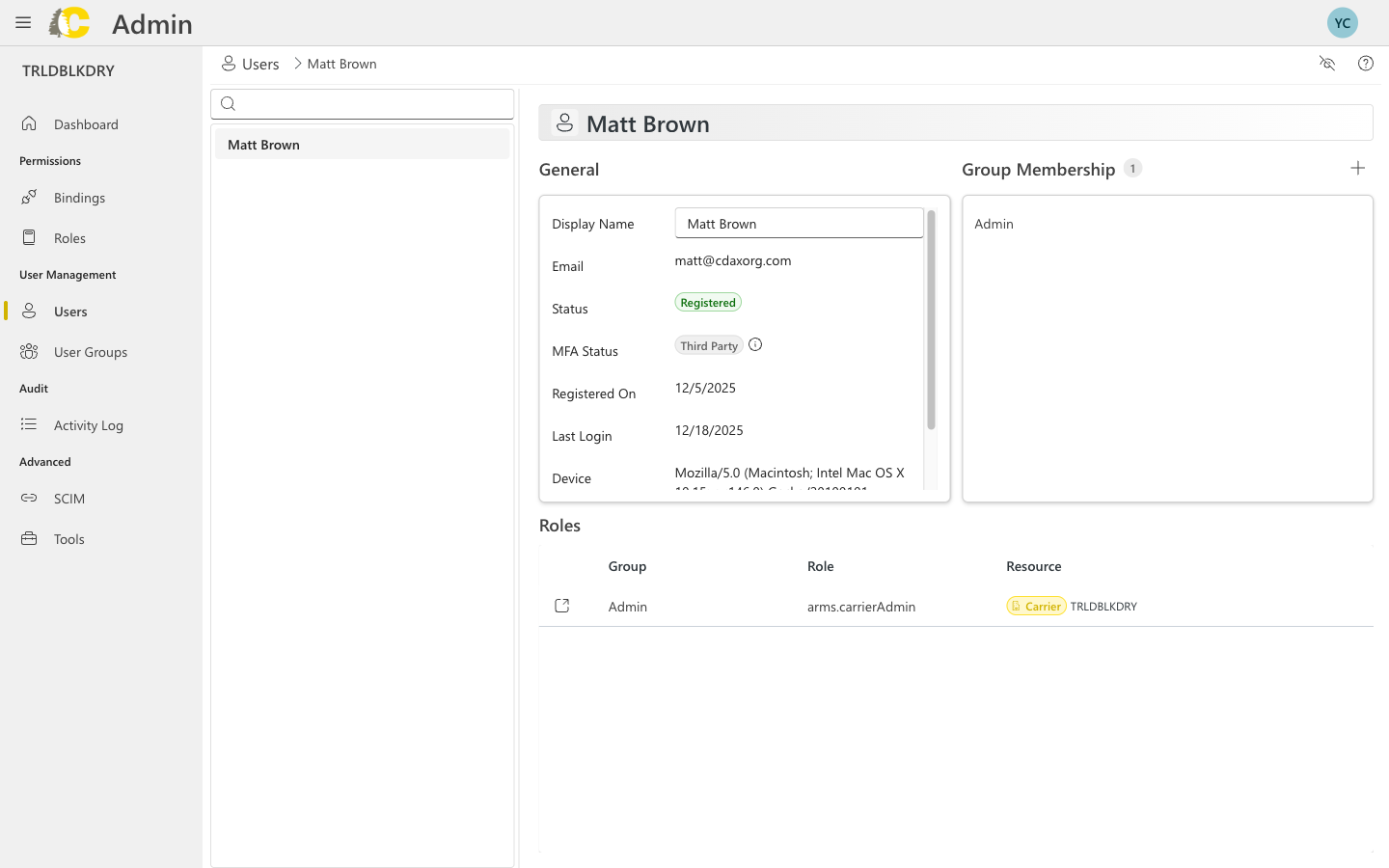
- Display name and email — How they appear in the system
- Account status — Registered, Pending, or Disabled
- MFA status — Whether multi-factor authentication is enabled
- Last login time — When they last signed in
- Group memberships — Which groups they belong to
- Role assignments — Direct roles (if any) assigned to this user
User status lifecycle
Users go through different states as they interact with Cedar. Understanding these states helps you manage accounts effectively.Cedar Managed Users
Go through Confirmed state when they click the email link, then complete registration to become Registered.
SSO Users
Skip Confirmed entirely — they go directly from Invited to Registered on first SSO login.
| Status | Description | Can sign in? |
|---|---|---|
| Invited | Invitation sent, waiting for user to take action | No |
| Confirmed | User opened the registration email link (Cedar managed only) | No |
| Registered | Account is active and fully set up | Yes |
| Invitation Expired | User didn’t respond within 2 weeks | No |
| Deactivated | Account has been disabled by an administrator | No |
Why SSO users skip Confirmed: SSO users authenticate through your identity provider (Okta, Azure AD, or Google), so there’s no separate email verification step. When they sign in via SSO for the first time, Cedar recognizes them as an external provider user and automatically marks them as Registered.
Reactivating users: If a user was previously Deactivated but has valid credentials (e.g., they previously completed registration), an admin can reactivate them back to Registered status.
SSO users vs Cedar managed users
There are two ways users can authenticate with Cedar. Understanding the difference helps you choose the right approach for your organization.- Cedar Managed Users
- SSO Users
Cedar managed users have accounts created and maintained directly in Cedar.How they’re created:
- Manually invited through the Admin Portal
- You enter their email, first name, and last name
- Use the Cedar login page
- Enter their email and password
- Optionally use MFA (if enabled)
- Users set their own password during registration
- Password resets go through Cedar
- MFA is configured in Cedar
- Small teams without an identity provider
- External partners or contractors
- Organizations not using SSO
Key differences at a glance
| Aspect | Cedar Managed | SSO |
|---|---|---|
| Account creation | Manual invite | Manual invite or SCIM (optional) |
| Password management | Cedar (Cognito) | Identity Provider |
| MFA | Cedar SMS-based MFA (optional) | Identity Provider handles MFA |
| Offboarding | Manually disable in Cedar | Manually disable, or via SCIM if enabled |
| Group sync | Manual assignment | Manual, or automatic via SCIM if enabled |
| Registration flow | Invite → Confirm → Register | Invite → Register (skips Confirm) |
Learn more: For SSO setup instructions, see the SSO Overview. For optional automated user provisioning, see SCIM Provisioning.
Best practices
Use groups for access management
Use groups for access management
Instead of assigning roles directly to users, add users to groups and assign roles to the groups. This makes access much easier to manage when team members change.
Check spam filters for invites
Check spam filters for invites
If someone isn’t receiving their invitation email, ask them to check their spam folder. Also verify the email address is spelled correctly.
Review MFA status
Review MFA status
For Cedar managed users, encourage enabling SMS-based MFA for extra security. You can see each user’s MFA status in their detail panel. SSO users’ MFA is managed by your identity provider.
Keep user information accurate
Keep user information accurate
Maintain up-to-date names and email addresses. This helps with auditing and makes it easier for colleagues to identify users.